scalander notes
Last edited: August 8, 2025- adding emails need sequential typing
- hitting enter should move on to the next page
- date selection
- “Monday next week” doesn’t NLP
- reading calendar output isn’t sorted
bugs
- reading other people’s calendars isn’t working
- need some information about that the heck is actually happening on the scheduling
- show other people’s overall availibliity in the scheduling page
- idea of “budget”
next actions
- scheduling multiple people is broken. ah.
- have the idea of a “meeting owner”, and we only reach out to them to confirm final date + have an ability to add a message (with templates); also allow the message owner to change to alternate schedules on that date
- the weight number doesn’t make sense—correct alt-text and make the number work
scalander notes
Last edited: August 8, 2025- adding emails need sequential typing
- hitting enter should move on to the next page
- date selection
- “Monday next week” doesn’t NLP
- reading calendar output isn’t sorted
bugs
- reading other people’s calendars isn’t working
- need some information about that the heck is actually happening on the scheduling
- show other people’s overall availibliity in the scheduling page
- idea of “budget”
next actions
- scheduling multiple people is broken. ah.
- have the idea of a “meeting owner”, and we only reach out to them to confirm final date + have an ability to add a message (with templates); also allow the message owner to change to alternate schedules on that date (have default notifications in the iCal invite)
- somehow remind people after the fact that the meeting is scheduled
- tie in evite abilities (this will be nice for your party, etc.)
- event planning built in? type in a budget and find vendors for the party.
- age range?
- the weight number doesn’t make sense—correct alt-text and make the number work
home page
- “the front page looks like that for an OB-GYN” — feels like ZocDoc
- it is also not that fun
- maybe some kind of memphis design
scalar multiplication
Last edited: August 8, 2025Scalar multiplication is the process of multiplying a scalar to an element in a set.
constituents
- A set \(V\)
- Some \(\lambda \in \mathbb{F}\)
- Each \(v \in V\)
requirements
scalar multiplication is defined by a function that results in \(\lambda v \in V\) (maps back to the space!) to each \(\lambda \in \mathbb{F}\) and each \(v \in V\).
additional information
scheduling
Last edited: August 8, 2025scheduling is the tool to figure out which thread can run. Because threads exist in different thread states:
- running
- blockde - waiting for an event like disk, network, etc.
- ready - able to run, but not on CPU yet
a scheduler needs to do the task of ordering ready threads to run, moving running threads to ready when it has ran for enough time. Possible pathways:
- ready => running
- blocked => running
- blocked => ready => running
You can’t go from ready to blocked because you have to do something to know you are blocked.
second moment of area
Last edited: August 8, 2025The second moment of area is a value which—given an origin—describes how point masses are distributed around that origin. (i.e. a number for how point masses are distributed). It is in units \(m^{4}\).
Take, for instance, the following picture:
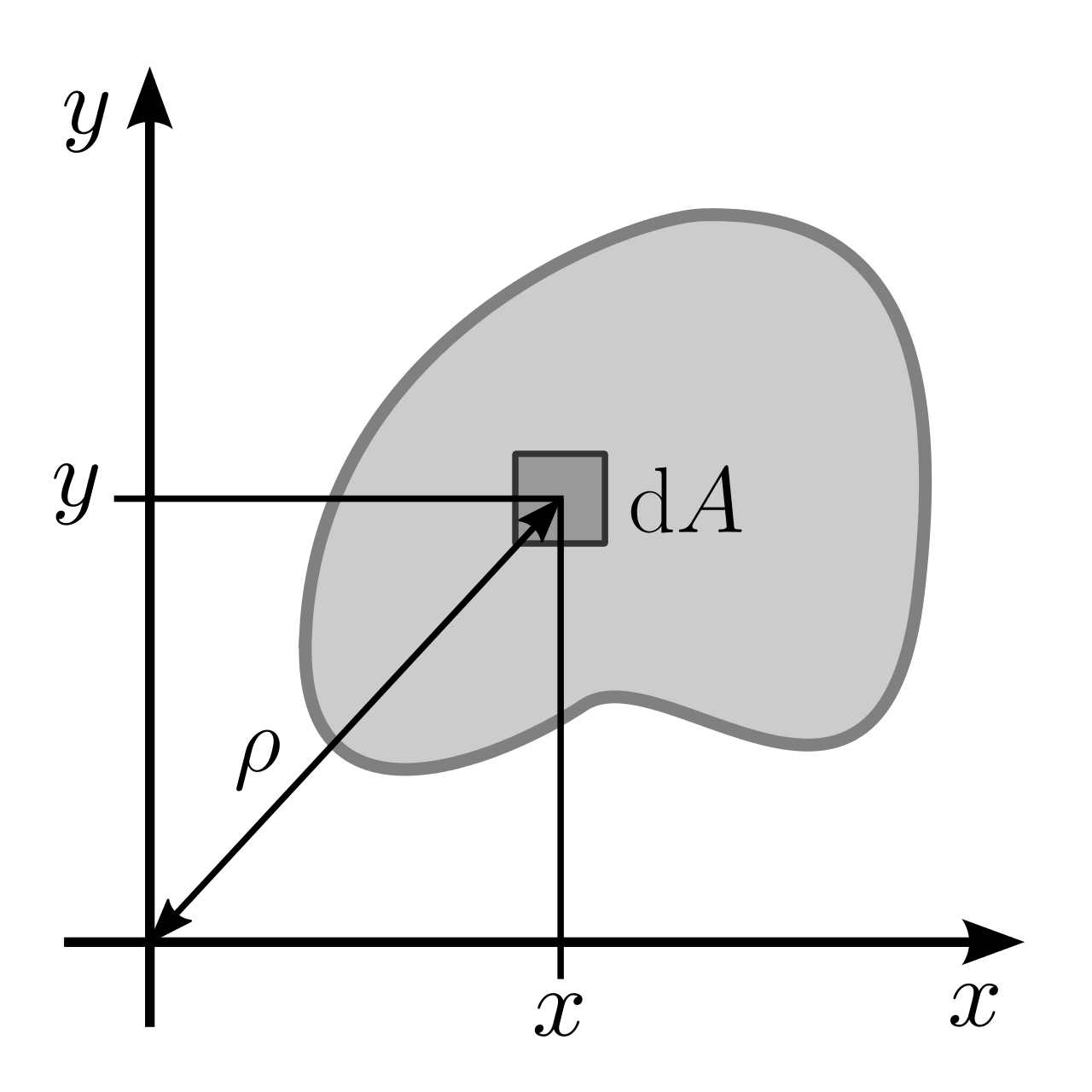
We have defined an origin at \((0,0)\) of the figure above. Furthermore, we have some \(\rho_{i}\) which is the distance from that origin to each of the infinitesimal areas \(\dd{A}\).
Then, the second moment of area is defined as: